
At alltasksIT, we’re committed to informing our audience with in-depth, actionable insights. This article dives into advanced topics we consult regularly, from secure cloud configurations to hybrid identity management. If you’re a technical professional, consider this page a valuable resource—bookmark it, read it at your pace, and, most importantly, act.
The Secure Cloud Business Applications (SCuBA) Project, an initiative by the U.S. Cybersecurity and Infrastructure Security Agency, provides guidelines and frameworks for improving cloud security. Designed initially for U.S. federal agencies, SCuBA’s principles are widely applicable, offering a robust framework for securing cloud environments like Microsoft 365.
This document contains dozens of carefully vetted links we’ve thoroughly studied, so you don’t have to. However, if you’re interested, feel free to explore them, and don’t hesitate to reach out for an assessment to see how your setup aligns with the framework we’re about to discuss
All our posts have a free offer? At the core of this article is the idea that you should care about your Microsoft Secure Score, it’ll tell you everything you need to know about this topic, most customers score about 50% when we first take them on, and we manage to get them to 80% pretty quickly with minimal fuss and no interupition leveraging the topics of conversation we’ve discussed below?
Feeling overwhelmed? Don’t worry. At alltasksIT, we’re here to provide the support you need. We can thoroughly review your cloud security posture and ensure your setup aligns with industry-leading standards, giving you the peace of mind to focus on what matters most.
Unlike our SEO-optimized content, this piece is crafted for those looking to deepen their understanding and enhance their cybersecurity posture. We’re often asked, “Aren’t you already doing this for us?” The answer is often no—not because it’s being neglected, but because the features of platforms like Microsoft 365 evolve constantly, requiring specialised projects to address the latest risks. This constant evolution keeps us on our toes, ensuring we’re always prepared to address the latest security challenges.
While some topics like MFA and email security are universally relevant, others cater to more complex needs like hybrid work environments. Regardless of your situation, this article has something for everyone, empowering you with the knowledge to keep your company secure. We’re here to inform and arm you with the tools to protect your organisation proactively and effectively.
This article is all about empowering you with the knowledge and tools to understand why hardening your Microsoft 365 (M365) environment is critical. It goes beyond the basics of what we can deliver through managed services alone. With M365 evolving continuously, staying on top of the latest security practices, configurations, and tools is essential. At alltasksIT, we aim to secure your cloud environment as much as possible within our managed services, but some security measures require a deeper, more hands-on approach. This guide walks you through advanced options to elevate your M365 security stance and tackle the areas that need a proactive, structured effort.
We get it; you’re busy and looking for a quick, actionable summary. Below are eight essential tips and strategies to help you harden your Microsoft 365 and cloud environments so you can dive right into the most critical points. Whether it’s visibility frameworks or security baselines, here’s a straightforward look at what matters most to keep your systems secure and resilient:
Start with foundational security controls to protect your environment.
Strengthening access points with MFA is an essential step in reducing unauthorized access.
Use Defender’s advanced threat detection capabilities to detect and respond to threats across email and collaboration tools.
Ensure privileged access protection and leverage conditional access to secure identities.
Manage user permissions, external access, and data loss prevention to protect collaboration channels.
Use eVRF to map and monitor visibility across critical areas, especially within Microsoft 365, to stay aware of potential blind spots.
Reinforce email security to prevent unauthorised access and safeguard against data breaches.
To mitigate exposure risks, Enforce policies around data sharing, guest access, and sensitive information labelling.
The Secure Cloud Business Applications (SCuBA) Project, led by the U.S. Cybersecurity and Infrastructure Security Agency (CISA), enhances cloud security for government agencies. Its goal is to unify cloud business application security configurations and best practices. SCuBA offers tools, frameworks, and guidance to protect sensitive federal data in cloud environments.
This project’s adaptable security measures support platforms like Microsoft 365 and Google Workspace, aligning with frameworks like Australia’s Essential Eight to bolster cybersecurity standards. SCuBA provides critical resources, including the Technical Reference Architecture (TRA), extensible Visibility Reference Framework (eVRF), and secure platform configuration baselines. These documents offer practical guidance for implementing robust cloud security across multiple environments
What’s all this really about, and why should you care? Think of SCuBA as a cheat sheet for keeping your cloud stuff safe. It’s like a guidebook from the pros on how to lock down your data and avoid cyber mishaps. We’re breaking it down so you don’t have to comb through a mountain of tech speak—just the essentials to keep your business secure in the cloud. Stick with us, and you’ll get the scoop on what matters!
Although SCuBA is primarily tailored for U.S. federal entities, it carries significant implications for cybersecurity practices globally. Australian businesses, in particular, should pay close attention to these guidelines, as Australia’s cybersecurity frameworks often reflect guidance from U.S. counterparts. This collaboration ensures that both countries can respond to emerging cyber threats in a coordinated manner, benefiting from shared knowledge and expertise.
Still with us? Great! Now, let’s get down to the nitty-gritty. It’s one thing to know why the SCuBA Project matters, but it’s another to understand how to apply its guidance in real-world settings. So, let’s dive into the tech specifics and walk you through practical ways we’re leveraging SCuBA to keep our clients secure. From eVRF to Microsoft 365 baselines, there’s plenty to unpack—and we’ll make sure you’re armed with actionable insights for each one.
The Technical Reference Architecture (TRA) is SCuBA’s backbone, providing a vendor-neutral framework for securing cloud business apps. It’s like a playbook on building a secure cloud setup using modern practices like zero-trust. When alltasksIT secures your applications—especially public-facing ones—we follow the TRA to align with top security standards. So, while you may not be diving into the TRA yourself, its principles are behind the secure cloud environments we build for you.
Technical Reference Architecture (cisa.gov)
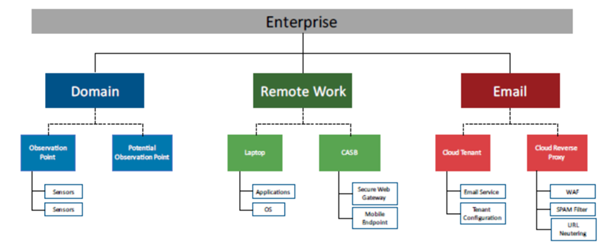
The extensible Visibility Reference Framework (eVRF) helps organisations see their digital security landscape clearly by identifying gaps in data visibility. For alltasksIT, eVRF is essential for assessing cloud security, especially in Microsoft 365. With a focus on data observability, it lets us map out critical areas and detect where threats might hide. The eVRF includes a Guidebook and workbooks—such as the Microsoft 365 workbook—which we use to ensure all key security surfaces are covered. This structured approach reveals unseen threats and aligns with what every organisation should consider for securing M365. Ready to dive deeper? We can customise eVRF principles to suit your security needs
Secure Cloud Business Applications (SCUBA) (cisa.gov)
CSSO-SCUBA-eVRF Spreadsheet-M365.xlsx (live.com) (check out the Attack Overlay)
Learn about auditing solutions in Microsoft Purview | Microsoft Learn
Office 365 US Government – Service Descriptions | Microsoft Learn
Office 365 US Government – Service Descriptions | Microsoft Learn
The SCuBA Project discusses secure configuration baselines for Microsoft 365 (M365) and Google Workspace (GWS), providing a set of essential security measures designed to help organisations mitigate risks and enhance their security posture. These baselines are adaptable to different security needs and include automation features that simplify implementation for IT teams. Covering core areas like email, collaboration, and identity management, these baselines empower organisations to secure M365 and GWS environments more effectively. Detailed configuration documents for M365 are available on GitHub, guiding teams in systematically applying these security measures
365 Defender for proactive threat detection and response. This cloud-based suite coordinates prevention, detection, and investigation across email, collaboration, and compliance tools, offering advanced threat detection capabilities. The baseline focuses on configuring Defender for Office 365 with recommended security settings via the Microsoft Purview compliance portal and the M365 Defender portal. This dedicated security layer provides foundational protection against phishing, malware, and other threats refer to Microsoft’s official resource page.
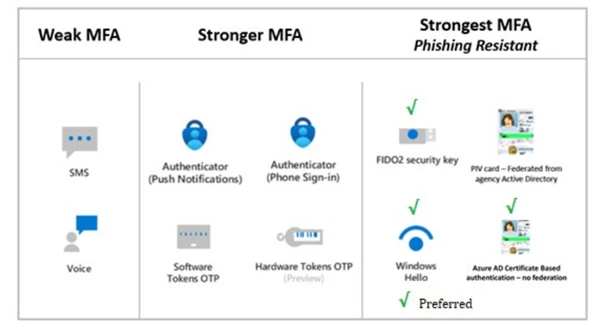
The AAD baseline policies address various security risks associated with user authentication, access control, and privileged roles. The baseline includes steps to block legacy authentication and leverage conditional access to secure high-risk accounts and sign-ins. Additionally, strong authentication methods, such as phishing-resistant multi-factor authentication (MFA), are recommended for enhanced security.
For technical details, the policies guide administrators in configuring baseline measures, including the use of Azure AD Identity Protection and enforcing MFA for privileged accounts. This foundational approach helps ensure that Azure AD environments are protected against unauthorized access and potential vulnerabilities. For complete policy instructions, please refer to the full baseline document on Microsoft’s security guidance page.
The Exchange Online baseline provides security measures to safeguard email communication, prevent unauthorised access, and mitigate potential data breaches. As a part of CISA’s Secure Cloud Business Applications (SCuBA) project, these configuration baselines are essential for organisations seeking to enhance the security of their email systems and minimise risks associated with email-based threats.
The baseline addresses various security areas, including automatic forwarding to external domains, Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), Domain-based Message Authentication, Reporting, and Conformance (DMARC), and multi-layered phishing protections. Each policy recommends disabling insecure settings, such as SMTP AUTH, and implementing strict controls to reduce vulnerabilities, like external sender warnings and Data Loss Prevention (DLP).
Administrators can configure these settings using the Exchange admin centre, Microsoft 365 Defender portal, and Microsoft Purview compliance portal. Refer to the complete baseline documentation on Microsoft’s Exchange Online security guidance page for technical steps.
The SharePoint and OneDrive baseline focuses on reducing security risks related to external sharing, link permissions, and custom scripts. As part of CISA’s Secure Cloud Business Applications (SCuBA) project, these policies help organisations to implement stricter access controls and prevent unauthorised access or data leakage.
The baseline recommends limiting external sharing to existing guests or people within the organisation, restricting file permissions to View-only by default, and enforcing expiration dates for Anyone links. Additionally, it mandates disabling custom scripts to prevent the execution of potentially malicious code on personal and self-service sites.
Administrators can configure these settings via the SharePoint admin centre and are encouraged to follow detailed setup instructions for each policy. For further configuration details, refer to Microsoft’s SharePoint and OneDrive security guidance.
The Power BI Secure Configuration Baseline provides guidelines for securing Power BI within Microsoft 365 (M365) environments. Developed as part of the Secure Cloud Business Applications (SCuBA) project, this baseline is intended to help federal agencies and organizations apply robust security controls tailored to their risk profiles. Implementing these baselines helps protect sensitive data, manage external access, and mitigate risks associated with data sharing and collaboration.
The Power BI baseline policies address various risks associated with data sharing, external access, and embedded visuals. Key areas covered include limiting data exposure through the Publish to Web feature, restricting guest access, securing sensitive information with sensitivity labels, and managing the use of service principals and ResourceKey authentication.
These policies guide administrators in configuring secure settings for data exports, external collaborations, and sensitivity labels, thereby safeguarding Power BI environments from unauthorised access and data leaks. The baseline also includes detailed steps for implementing each policy, helping organisations ensure their Power BI deployments adhere to best practices in data security. Refer to the Power BI Security Baseline document in Microsoft’s security guidance resources for complete configuration details.
The Power Platform Secure Configuration Baseline outlines essential security controls for Microsoft 365’s Power Platform suite. Developed under the Secure Cloud Business Applications (SCuBA) project, this baseline helps federal agencies and organisations secure low-code applications, automated workflows, and data integrations. Implementing these baselines enhances data protection, mitigates risks associated with unauthorised data access, and maintains control over Power Platform environments.
The Power Platform baseline policies cover various security controls across the suite’s tools, such as Power Apps, Power Automate, and Power Virtual Agents. Key areas include limiting environment creation to administrators, enforcing Data Loss Prevention (DLP) policies, configuring tenant isolation to prevent unauthorized cross-tenant access, and enabling Content Security Policies (CSP) to protect against web-based attacks.
These policies guide administrators in configuring secure environment settings, restricting access to connectors, and managing external access to data and services. This baseline ensures Power Platform environments adhere to best practices for data protection, minimizing risks related to data exposure and enhancing overall platform security. For complete details, refer to the Power Platform Security Baseline document available in Microsoft’s security guidance resources.
The Microsoft Teams Secure Configuration Baseline outlines essential security controls for collaboration within Microsoft 365’s Teams platform. Developed under the Secure Cloud Business Applications (SCuBA) project, this baseline helps federal agencies and organizations protect meetings, chats, and file sharing in Teams. By implementing these baselines, agencies can enhance user authentication, manage external access, and reduce data exposure risks.
The Teams baseline policies address various security concerns across meeting settings, external user access, app management, data loss prevention, and malware scanning. Key measures include restricting meeting controls for external participants, limiting app permissions to approved apps, and enforcing data loss prevention policies to safeguard sensitive information. The baseline also covers malware scanning for attachments and safe link protection to prevent access to known malicious sites.
These policies guide administrators in configuring secure settings to control user interactions and manage external access effectively. This approach ensures that Teams environments comply with best practices, reducing risks related to unauthorized data access and enhancing overall platform security. For full configuration details, refer to the Microsoft Teams Security Baseline document available in Microsoft’s security guidance resources
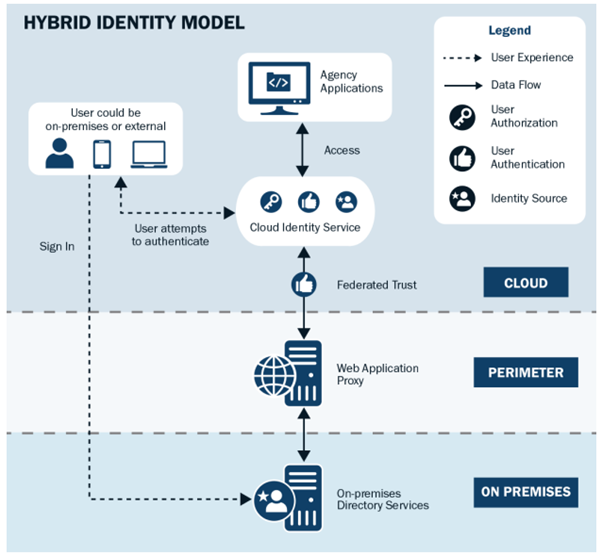
The Hybrid Identity Solutions Guidance from CISA outlines various strategies for managing identity in a hybrid environment, where on-premises and cloud-based systems must interact seamlessly. This document serves as a foundational resource for agencies to understand the available options for hybrid identity management and the potential challenges and methods to mitigate them. The guidance is part of the Secure Cloud Business Applications (SCuBA) initiative, which aims to enhance identity security across federal agencies.
The guidance explores several hybrid identity solutions, including federation, pass-through authentication, and password synchronisation, each with unique benefits and trade-offs. Additionally, it examines multi-factor authentication (MFA), single sign-on (SSO), and password-less authentication options such as FIDO2, focusing on security and interoperability. By using these modern authentication techniques, agencies can move closer to a zero-trust security model, which reduces dependency on traditional passwords and increases security resilience.
Agencies are encouraged to leverage cloud-based identity services and integrate these modern authentication options. This document offers insights into aligning agency identity solutions with zero-trust principles, as outlined in federal cybersecurity mandates. It emphasises the importance of adopting secure, cloud-first identity practices for robust, efficient, and secure identity management. For full details, consult the Hybrid Identity Solutions Guidance available on CISA’s website.
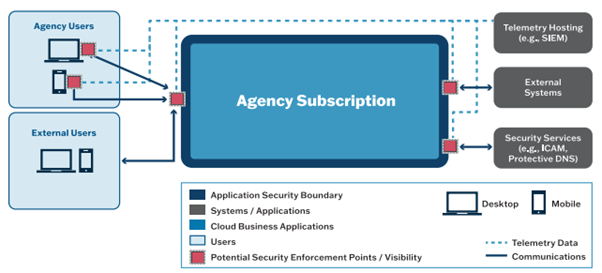
The image below illustrates conceptually how your organisation has users accessing potentially sensitive information and the services with your Microsoft 365 subscription to secure your data. These components of the Microsoft 365 platform often come out of the box, not “hardened” or simply, with minimal security defaults turned on.
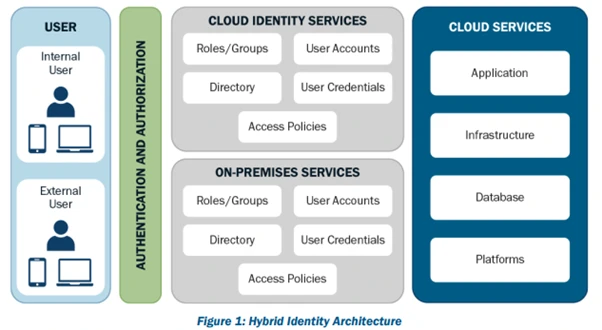
The Hybrid Identity Model applies to customers who still maintain servers onsite, and the image below describes the CISA guidance for best practices on securing your external users and applications to keep your data protected.
We’ve covered a lot of ground, from the fundamentals of SCuBA to specific security baselines that strengthen your M365 environment. While managing the complexities of cloud security can feel overwhelming, remember that you don’t have to navigate it alone.
At alltasksIT, we’re here to support you every step of the way, from understanding these essential concepts to implementing advanced security practices.
We aim to either help you build a resilient, well-protected cloud environment that keeps pace with emerging threats if you have an IT Team of your own, or we take care of this for you in our Managed Services. If you’re ready to take the following steps to harden your M365 setup, we’re here to help make it happen.

Chief Customer Officer (CCO)
Mark Boyd is a Chief Customer Officer (CCO), plays a key executive role responsible for overseeing the entire customer experience within alltasksIT. The CCO serves as the voice of the customer at the highest levels of the company, ensuring that customer-centric strategies are developed and implemented across all departments.