
Whether we like it or not, technology hiccups happen. Chief Information Officers (CIOs) often carry a reputation for fire-fighting, but they can (and should) do much more than respond to incidents. After all, the “I” in CIO should stand for Information, Infrastructure, Innovation, Integration, and Intelligence – not Incidents!
With the increasing complexities of flexible work, a glut of data from SaaS applications, and the pressure of looming security regulations, CIOs are in a prime position to defend and redefine. They can influence culture, governance, and business transformation – and that’s precisely why we’re hosting a webinar on the 10 tools CIOs should be investigating now to protect their organisations’ digital assets. (Intrigued? The registration link is coming soon!)
One of the most effective ways CIOs can drive positive change is by developing a resilience-driven framework that prioritizes strategy and governance. Instead of merely dusting off continuity plans when a crisis arises, CIOs should have a living roadmap of best practices, clearly assigned accountabilities, and internal control processes that flag issues long before they become significant outages.
This includes:
Building collaborative relationships with the CISO to ensure cybersecurity and infrastructure decisions are in sync;
Implementing robust data management policies to track usage and potential vulnerabilities across the organisation’s technology stack;
Working with finance and legal to comply with fresh security legislation in Australia (see our articles here: [Insert placeholder text for hotlink]); and
Maintaining a flexible yet structured environment where changes are tested and validated continuously rather than as a last-minute reaction to a looming crisis.
The numbers on downtime are sobering. Many organisations report that even a few hours offline can cost them hundreds of thousands of dollars, not to mention reputational damage. A strong governance framework, supported by routine audits and role-based access policies, ensures that the “I” in CIO remains associated with Infrastructure and Intelligence, not the dreaded “Incident.
Before you think you’re immune or you run a tight ship, remember that in 2024 alone, Australian organisations were hit by cyber incidents at a rate of more than one attack every single day—precisely 500 recorded events, ranging from ransomware to distributed denial-of-service assaults. Even big-name brands you’d immediately recognise (think Panasonic and Nissan, who depend on their reputations to keep customers loyal) weren’t spared.
And it’s not just Australia: ASEAN logged 2,829 incidents, India hit 3,936, the Middle East tallied 3,583, the Caribbean saw 66, the United States soared to 5,978, and Europe—spurred by the ongoing conflict in Ukraine—topped the list with 10,429. If that doesn’t serve as a wake-up call, consider that some of these cyber attacks resulted in massive data breaches and costly downtime for organisations that believed they were well-prepared.
In truth, the work is never finished. If you don’t plan proactively, strengthen your defences, and continually adapt to emerging threats, you’re always an incident waiting to happen. It’s not a matter of if but when.
Looking closer at the Australian landscape, the stakes remain high. Even though the ACSC’s Essential Eight is touted as a baseline for best-practice cybersecurity, many organisations still fail to adopt critical elements like immutable backups—where data is locked against unwanted edits or deletions—and robust application control mechanisms that tightly govern which code can run in environments holding sensitive information.
Budget constraints and time pressures are often cited as barriers, but if you’re operating more like a Chief Incident Officer than a Chief Information Officer, are you truly doing the right thing for your business?
Immutability alone can decide whether to restore your systems after ransomware or deal with devastating data loss that tarnishes your brand. Application control is essential to prevent unauthorised or malicious processes from taking root. Ultimately, ignoring these measures invites further incidents—when, not if.
Be the Chief Information Officer you were born to be.
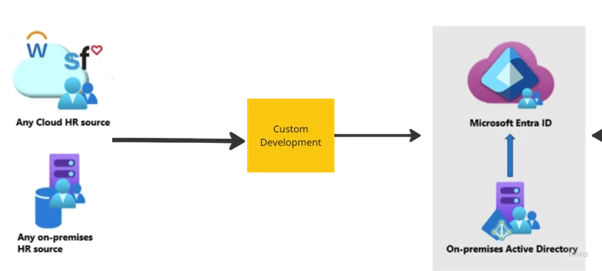
Automatically provisioning the vast majority of new employees based on data in the HR system.
Ensuring timely updates for employees transitioning roles.
Enabling SSO integration so users seamlessly access various systems with consistent credentials.
AlltasksIT’s end-to-end solution introduced an automated synchronisation process, dramatically reducing manual intervention and administrative workload. Key components included:

Understanding these dates helps you plan upgrades before support ends, ensuring your systems remain secure and efficient.
By partnering with alltasksIT’s software development team, Australia’s leading automotive retail chain successfully automated its HR directory synchronisation across Azure AD and Active Directory. The project showcased alltasksIT’s ability to deliver secure, high-impact solutions in complex, tightly controlled environments—ultimately improving operational efficiency, data accuracy, and employee satisfaction.
With a laser focus on secure coding practices and real-world applicability, alltasksIT continues to expand its software development capabilities, taking on projects that streamline processes and empower businesses across Australia. For organisations seeking a partner to tackle multi-faceted technology challenges, our team stands ready to deliver solutions that truly make a difference.

Chief Customer Officer
Mark Boyd is a Chief Customer Officer (CCO), plays a key executive role responsible for overseeing the entire customer experience within alltasksIT. The CCO serves as the voice of the customer at the highest levels of the company, ensuring that customer-centric strategies are developed and implemented across all departments.