Huntress Managed EDR
Get headache-free endpoint detection and response (EDR) that’s fully managed by Huntress 24/7 Security Operations Center (SOC)
Overview
Traditional IT security tools like antivirus and firewalls are designed to prevent cybercriminals from breaking into your network. While these defenses remain important, hackers are constantly finding new and innovative ways to bypass them and infiltrate SMB networks.
What happens when a hacker slips through undetected? How long will they remain hidden in your environment? What sensitive information will they capture? And when will they deploy ransomware to fully encrypt your systems?
Explore the hidden risks and learn how to protect your SMB network from evolving cyber threats. Stay one step ahead with our advanced security solutions.
HOW EDR WORKS
Help users trust who’s in their inboxes. Secure Microsoft 365 identities and email environments on our fully managed, multi-layer platform.
COLLECT
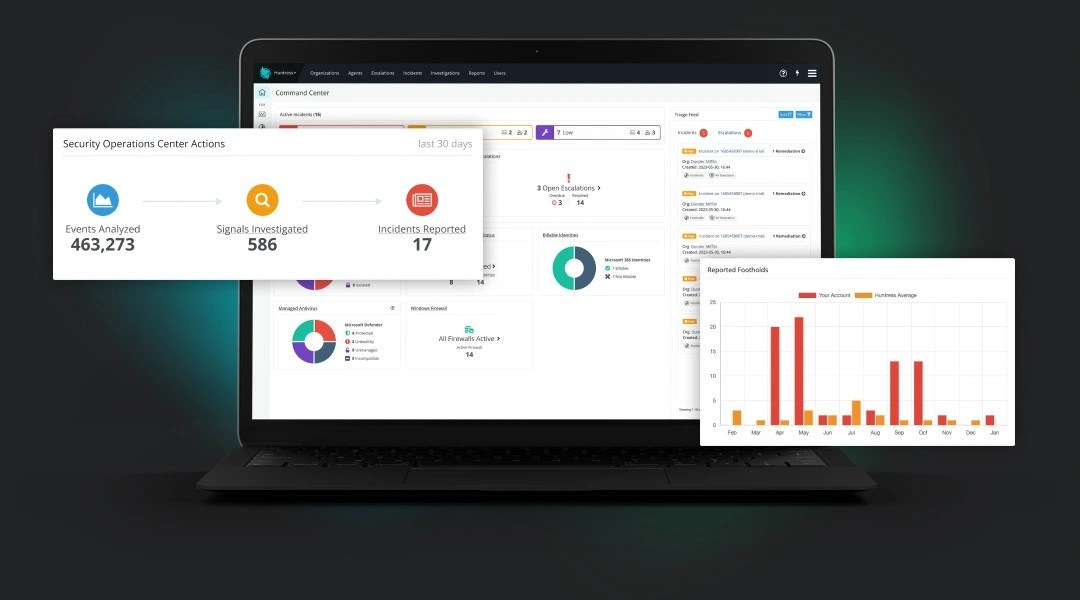
Our software collects data from your desktops, laptops and servers, and sends it up to a cloud-based engine for automated review. This process is invisible to users.
ANALYSE
Once Captured, our threat operations team manually reviews suspicious and potentially malicious activity to eliminate false positives and identify real threats to your network.
REMEDIATE
If an active threat is present, our team will isolate and remediate any infected machines. We'll also provide you with easy-to-follow instructions if additional work is required or if we need to coordinate with you directly.
Huntress Managed EDR
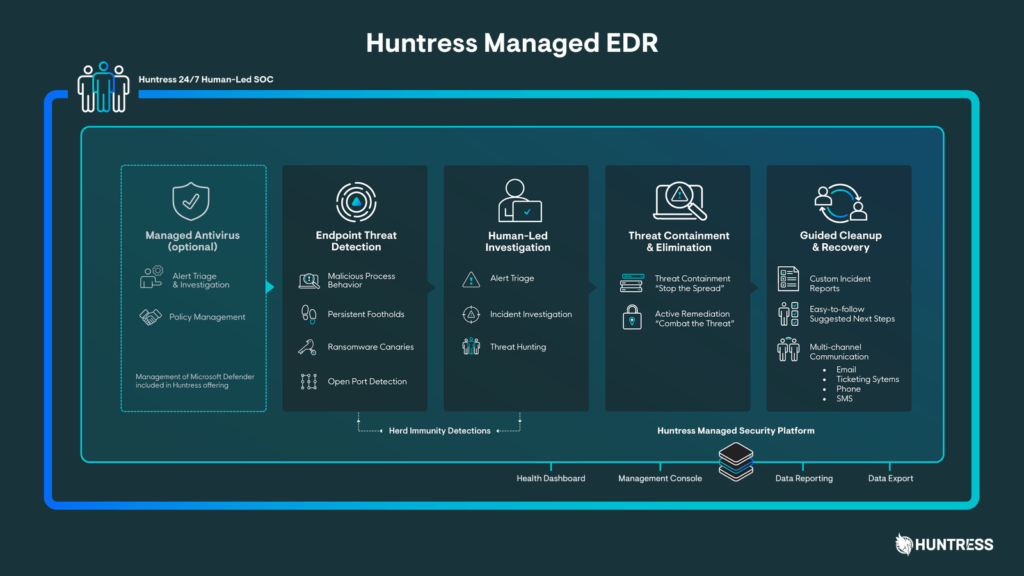
Huntress Managed EDR is both built and managed by Huntress team, with 24/7 detection and response from our human-led SOC. Huntress cybersecurity experts investigate suspicious activity in your environment to eliminate false positives and stop attackers before they do any damage.
EDR Key Capabilities
Learn about capabilities that make it easy to protect endpoints with Huntress Managed EDR.
Persistent Footholds
Hackers love hiding in plain sight. Managed EDR identifies the abuse of legitimate applications and processes that attackers use to stay hidden within your Windows and macOS environments.
Malicious Process Behavior
Attackers change their tools all the time, but their techniques stay consistent—that’s why we focus on behavioral analysis to identify and stop shady hacker activity.
Ransomware Canaries
Like a canary in a coal mine, the Huntress SOC monitors small, lightweight files for early indication and detection of ransomware.
Open Port Detection
Stop attacks before they start. Managed EDR strengthens your perimeter defenses by finding exposed entry points before attackers do.
Managed Antivirus (optional)
Swap out your current AV with the built-in version of Microsoft Defender Antivirus, and Huntress will manage it for you at no additional cost. Don’t want to use Defender? No problem. Huntress runs side-by-side with almost every AV.