
As a starting point, we’re giving you a valuable tool: a downloadable template for self-auditing your Essential8 compliance. This template, used in our professional audits, offers insights for everyone—from techs seeking granular control details to executives looking for high-level alignment with cybersecurity maturity.
Aligning with Essential8 is not a one-time achievement; it requires a dedicated, ongoing effort to maintain compliance. Without a structured, calendar-based approach, achieving sustained alignment is impossible. In other words, compliance is not a checkbox—it’s a daily, weekly, monthly, and annual commitment to rigorous security practices.
To truly stay aligned and secure, you must embed these practices into your organisation’s regular operations. Here are some time-bound activities essential for maintaining Essential8 alignment. Note that this is only a subset of all necessary controls, but these practices highlight the level of dedication required:
Protecting your business from cyber threats involves more than just buying the right software. It requires a holistic approach that includes both technological and human elements. Here’s how you can fortify your defences:
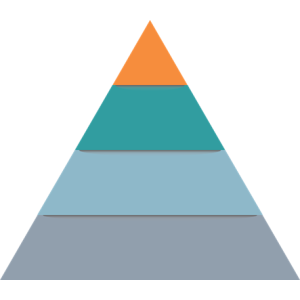
For those implementing Essential8 in their organisation, the McKinsey Pyramid Principle can simplify the framework’s structure and aid stakeholder communication. This principle advocates a top-down approach to thinking and communicating, which is well-suited to the Essential8 framework.
Visualize the Essential8 framework as a pyramid:
You have your overarching maturity level for each control area. For instance, what is your organisation’s maturity level for application control? Are you at Maturity Level 1, where basic restrictions are in place, or Maturity Level 3, where robust controls and extensive logging are fully integrated?
You have individual control requirements, such as patching applications or limiting administrative privileges. These are the building blocks of each control, and they provide a more detailed understanding of your compliance standing.
You find the detailed actions required to meet each control, like configuring software settings, applying patches, or analysing cybersecurity logs. This is where the technical implementation happens, and where your organisation can understand exactly what is needed to achieve each maturity level.
By working from the top down, you get a clear view of your overall alignment and then drill down into the specifics. This method allows you to approach Essential8’s requirements systematically, helping you assess and improve your security posture over time.
Executive Summary
What’s your overall attainment? This is what company executives want to see.
What’s your attainment per control?
What is the headline of attainment against each control for the eight controls?
What is the detail of each control?
Here you get technical; each control has its own unique requirements guiding you on what you need to do to be compliant.
Appendix & Support Evidence
Then, provide evidence, screenshots, and detailed summaries of our findings.
While some vendors claim their tool alone can ensure compliance, Essential8 requires a variety of tools. As an MSP, we leverage a suite of applications to meet Maturity Level 3 standards for our clients, including:
Intune, Airlock (ThreatLocker)


N-Able, Microsoft WSUS, Intune


Microsoft 365 Advanced Threat Protection

Airlock, ThreatLocker, and other hardening tools


Delinea Secret Service

N-Able, Microsoft WSUS, Intune


Duo Security, Microsoft MFA


Veeam, AvePoint


Chief Customer Officer (CCO)
Mark Boyd is a Chief Customer Officer (CCO), plays a key executive role responsible for overseeing the entire customer experience within alltasksIT. The CCO serves as the voice of the customer at the highest levels of the company, ensuring that customer-centric strategies are developed and implemented across all departments.