
How many applications are your staff using—and do you know the risks they pose? This post delves into the hidden world of “shadow IT,” exploring security blind spots, compliance concerns, and the surprising ways employees connect new apps to your environment. Discover how Nudge Security helps you regain visibility, improve data protection, and ensure compliance—all while asking crucial questions about what’s lurking in your SaaS ecosystem.
At first glance, it might seem straightforward: the IT Department is responsible for setting up all our applications.
End of blog post. Thanks for reading.
But wait, there’s more.
For the business-focused readers of our blog, your users are connecting applications to your business, and you have no way of knowing what they are doing or tracking it. Your users can also connect applications to your business data, and you cannot know what those applications have access to.
Until now.
Software as a Service Applications (SaaS apps) are running the planet your business is running on them. Businesses are expected to increase spending on software applications by at least 17% in 2024/25. It’s high time we start documenting what applications we use in business, why we use them, what they cost, and how we secure them.
Your business will have dozens of software applications across all departments in your business, and you have no way to govern them. That is what is happening, and we are here to fix that.
Do you run projects for your clients?
Maybe your staff used their email to connect Confluence, Asana, or Trello to your Microsoft 365 environment. Do you know what those applications can see? These applications know more about your business’s private data than you know. Why do you use three different tools that do the same thing? Do you even know if you have this problem?
What if a user in your organisation downloads a productivity tool that connects to Outlook to manage your business contact lists? For that tool to work, it has to temporarily read and store all the emails that belong to that person. What if that data sits in a data centre in a foreign location with relaxed data access laws? What if that tool is ever hacked?
Your data now belongs to someone else.
A new partnership at alltasksIt has formed, a partnership that lets us know exactly what is connected to your cloud environments, with what permissions, and who has signed up, for what, when, and (nudge nudge), why? We have selected Nudge Security as a partner because of its clear focus on helping organisations discover, manage, and govern the full range of their SaaS usage. Their approach to SaaS security for modern work stands out for its ability to uncover every cloud and SaaS asset in minutes. By working with Nudge Security, we can now identify shadow IT activity, secure unmanaged accounts, and bring SaaS sprawl under control.
Alright, let’s dive in. Look at the image below, a live example of alltaskIT’s top application users. We do highlight there’s no sensitive data below, they are really people in our organisation, doing real work, using applications that assist them to do their jobs. We have no problem with people using whatever applications they like but we do use Nudge Security to keep us across what they are using so we can enforce MFA, and make sure they vendors our people want to use, practice great operational security.
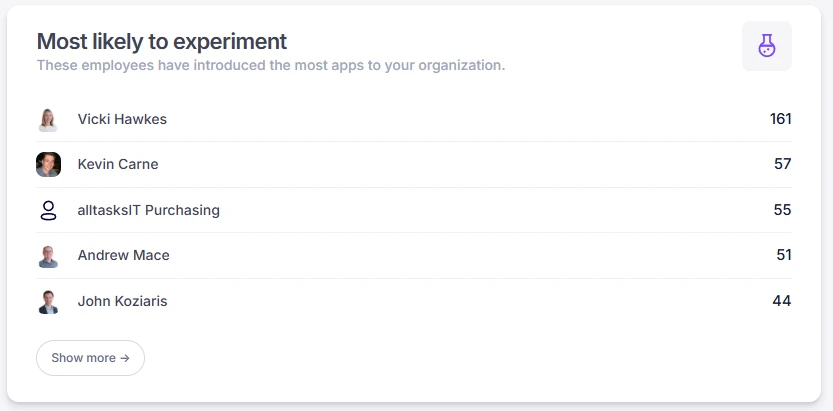
Vicki Hawkes, the CFO of your organisation, has used her work email to sign up for 161 different applications over the years.
We know what you’re about to ask. Does our CFO use 161 different apps? No, she does not. However, as a 30-year veteran of the organisation, Vicki has used her all-tasks email address to sign up for personal, non-work-related services. We don’t have a company policy on this, and Vicki is one of the company owners, so even if we did, rules are made to be broken.
But there IS an opportunity here to educate a user on the risks.
Vicki signed up for Woolworths and Coles for online shopping and used her alltasks email address. Let’s say Vicki used the same password for her service for Trello, a project management tool to keep her daily tasks on track.
It is typical for the IT team to have no idea Vicki uses any of these things. Why should we? We aren’t the police!
Then Woolworths gets hacked. Vicki’s password is leaked.
A good hacker will see the Woolworth’s breach, and strip away non Gmail/Hotmail accounts from the breach, and then actively try to logon to the types of apps businesses use in the hop there is password reuse and no MFA.
It’s called Credential Stuffing, and it’s more common than you think.
The hacker discovers that Vicki has a Trello account. The account has no MFA turned on. So they log on without anyone being any the wiser.
Vicki’s Trello account has sensitive customer information.
That information is now unfortunately very public and is a notifiable database breach according to the OAIC. Company Directors are financially and legally liable in the event precautionary measures were not taken to avoid this scenario.
Consider the everyday reality of your busy business.
Over time, these individual choices add layer upon layer of complexity.Each new app might have legitimate business value but can also access organisational data, read files, and integrate with core systems. Without a centralised way to track them, oversight is lost.
This sprawl leads to real risks. Sensitive information may be stored offshore. Offshore data isn’t subject to the same laws that govern Australian data sovereignty
Data may be shared with third-party vendors whose security practices remain unclear. Certain apps may lack multifactor authentication or fail to comply with your organisation’s security guidelines.
How do you even track multifactor authentication compliance aligned to Essential8 standards if you don’t know how many hundreds of applications your organisation uses?
Nudge Security. That’s how.
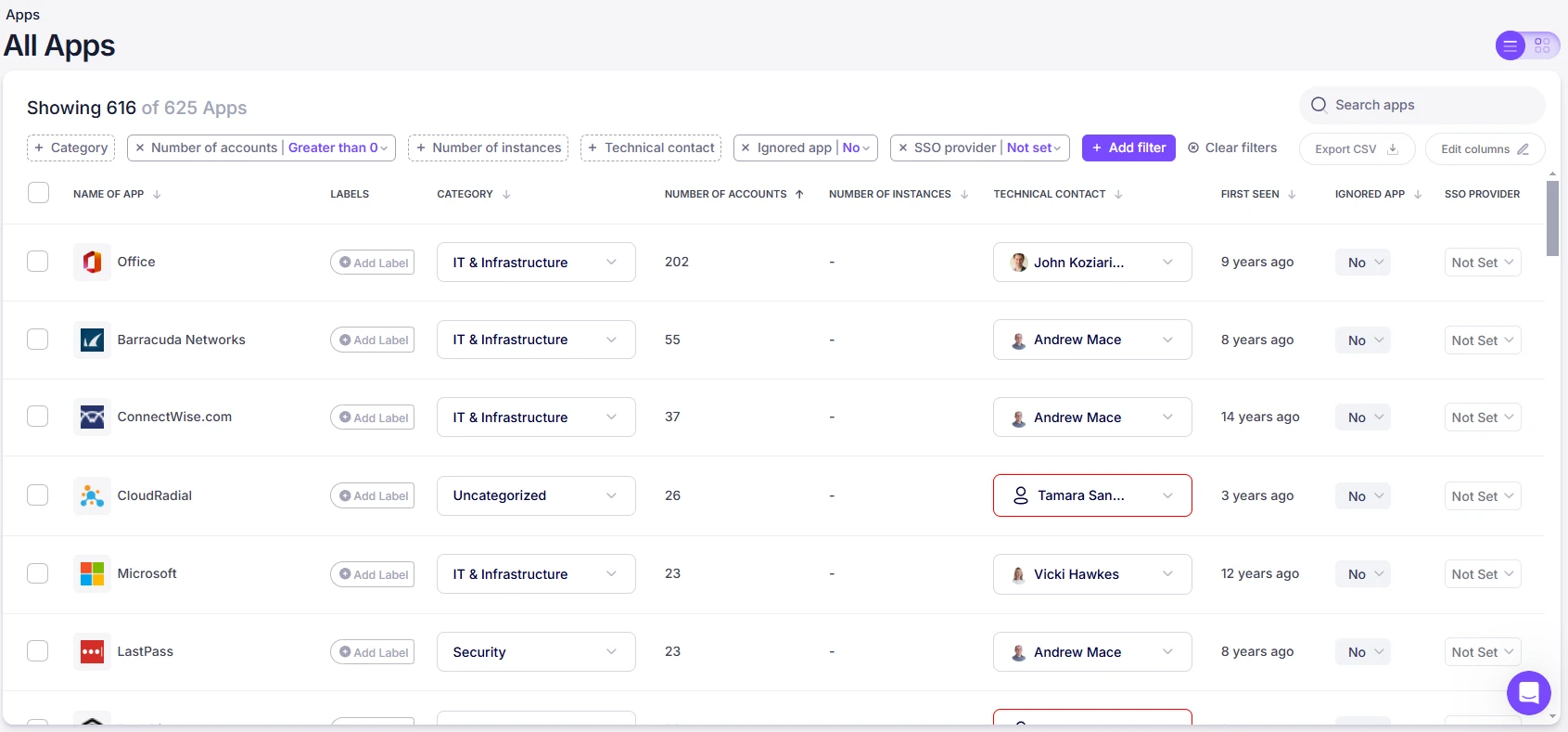
Consider the screenshot below.
We know every one of these services are protected with MFA/SSO so as a business, we are generally safe. Until Nudge Security however, we lacked a single pane of glass to see how compliant we are. Now, as an operational activity, our IT Team can manually mark them as protected and ensure all users in our organisations have MFA configured correctly.
If we spot an application in this list we don’t know about, we can nudge the end user asking them for business content on why they are using the application and work to securing it.
This exercise previously was either impossible or manual. We can now build out compliance reports for our board, directors, auditors, and insurers with the click of a button, AND we know we are safe online.
Even if your IT team knows where to look, there may be too many services to assess manually. The issue is not a lack of awareness but the sheer volume of services and the challenge of addressing them before problems arise.
Their solution helps reveal every SaaS asset connected to your environment, from popular collaboration tools to niche services a single team member signed up for last year. With this visibility, managing risk, streamlining usage, and ensuring that sensitive data is protected becomes possible. This is vital for adhering to frameworks such as the Essential 8, where comprehensive control and oversight of your digital environment are key objectives.
The screenshot below highlights any issues we might have with either our applications, or our EntraID/Security groups that govern access to them.
The reality is the score is never 100%, in fact, we trialled this on a few of our customers and they were <60% because IT Teams and MAnaged Service Providers alike, have never had a platform that goes into this amount of depth to deep dive secure a set of applications against industry best practice.
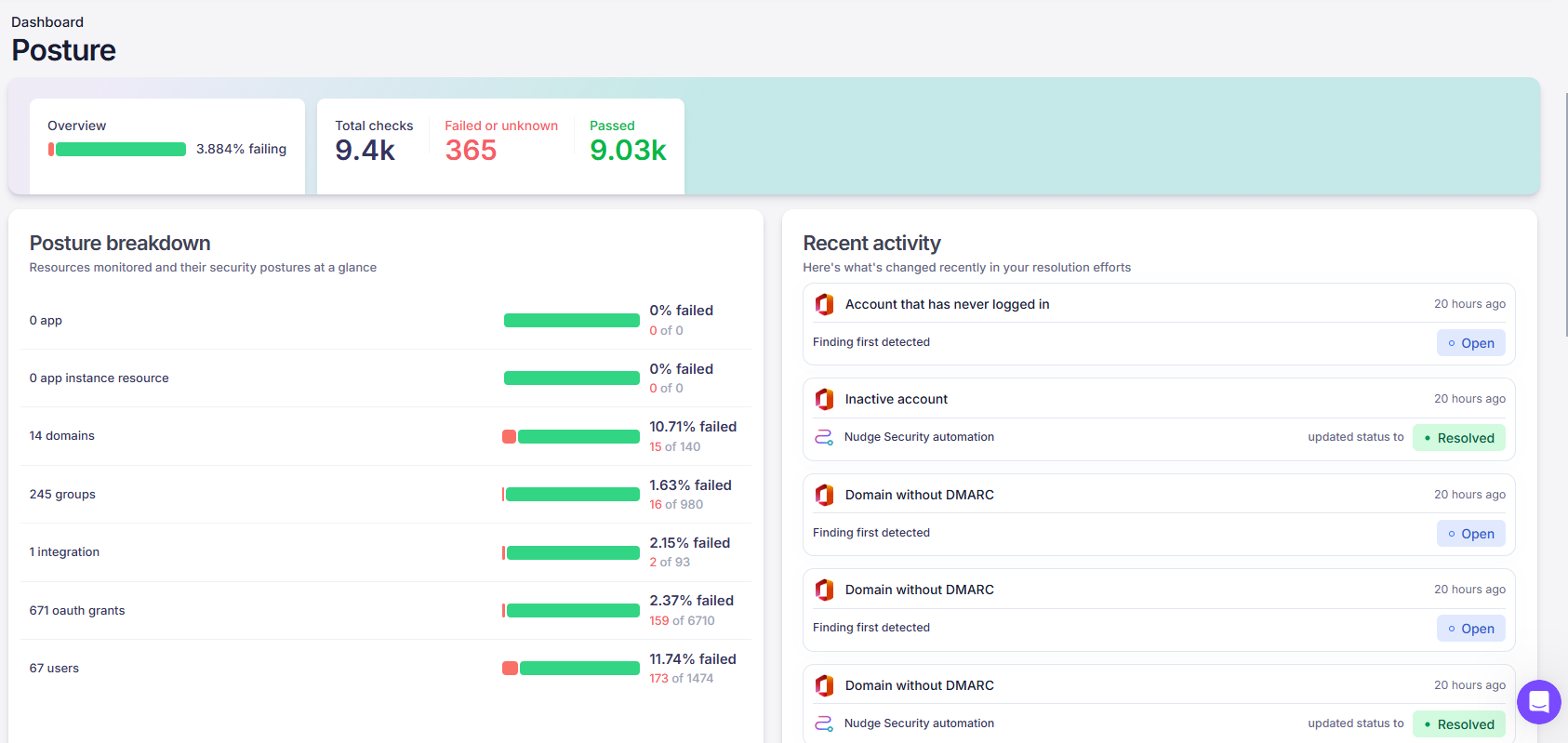
We are a company of just over 30 people. The numbers below show how a modern business can get caught up in a world of digital sprawl.

This breadth might sound alarming, but it can be controlled with the right management approach.
When we introduced Nudge Security to a select group of our customers, the results were telling.
One manufacturing client discovered applications they shouldn’t have allowed into their environment, which could read every document and email the customer ever produced, in the name of convenience, to help them file their doucments in a document library.
Another client in the entertainment sector uncovered dormant but still connected accounts and applications, each representing a potential vulnerability if those accounts or applications were ever compromised. With this insight, they could retire unnecessary services, tighten permissions, and secure their data.
In our environment, we recently reviewed applications we connected seven years ago and still use.
Do you know how some of your applications are connected to your environment?
Do you still use them?
Is the staff member who used the product still with your organisation?
If you don’t know the answer to these questions. You need Nudge Security
Just because a staff member leaves doesn’t mean the application can’t read your entire Microsoft 365 Library.
In the example below, let’s say we no longer use Datto; why is it still connected to our environment?
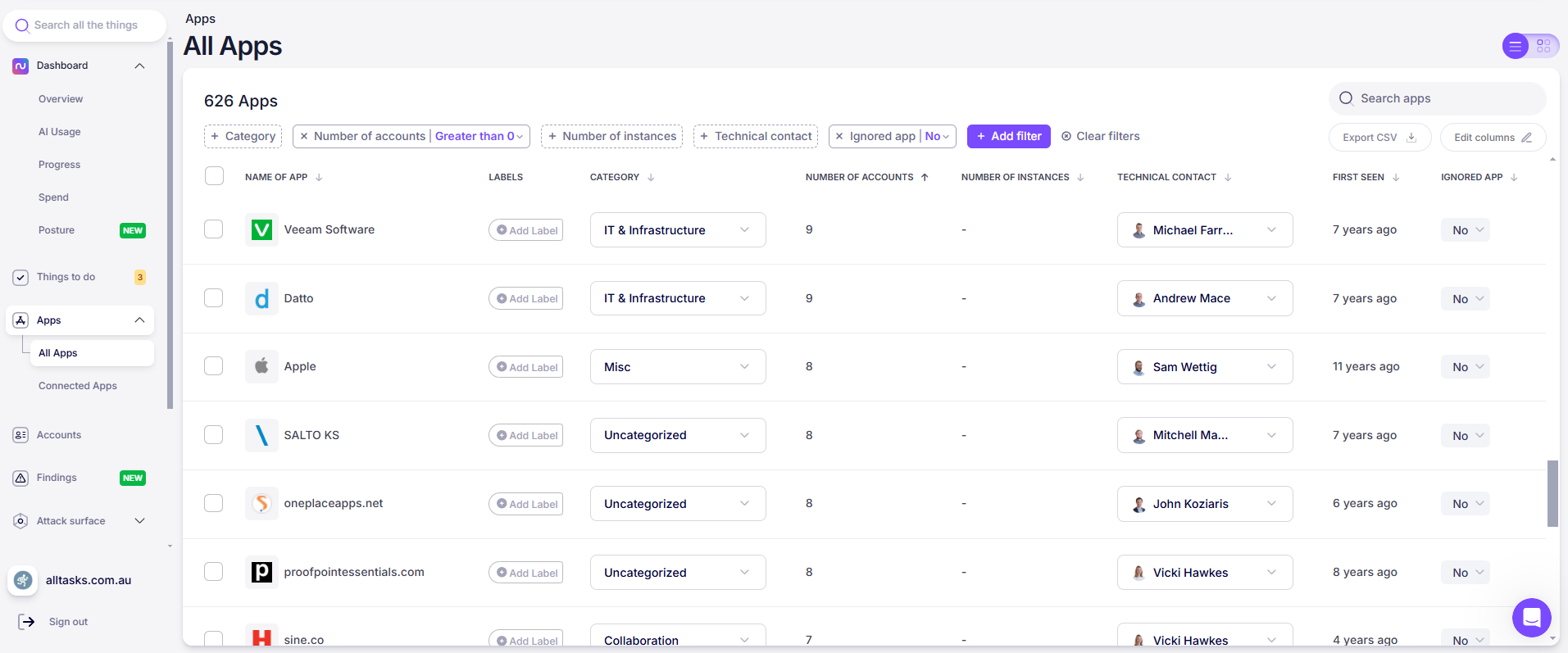
An employee in finance might adopt an AI-driven analytics platform that stores customer data abroad without the protections required by your compliance policies. Let’s pick on Kevin, one of our Account Executives. He signed up for an AI tool that is well-known and safe, but he’s not allowed to put customer data into these platforms based on an unwritten company policy.
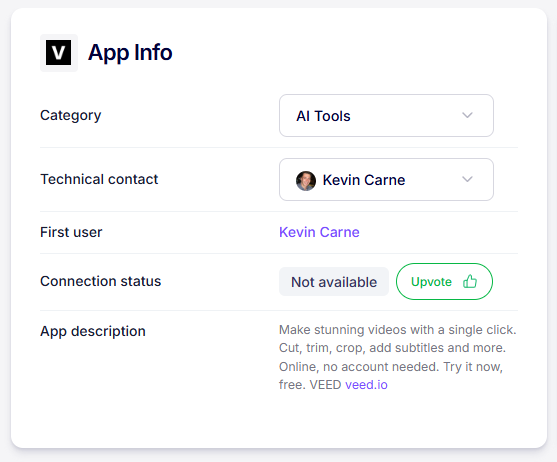
We use the platform to gain awareness he’s using it, and we can Nudge him to ask him to provide more information about the platform so we can continue to support it, or block it and find a safer alternative.
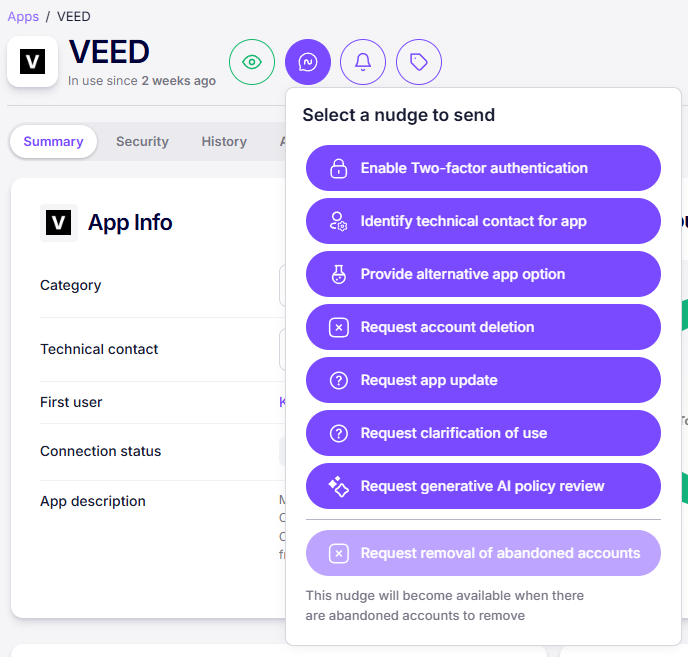
Nudge Security will alert you that your staff member signed up for Chat GPT, and you risk oversharing sensitive data. Maybe CoPilot was a better choice for them? Maybe you don’t have an AI Adoption policy in your organisation. You could use Nudge Security’s built-in Policy documents to have users sign and accept digitally that while they are allowed to use these AI tools, they are not to put sensitive customer information in them.
Automated acceptable use policies for a dynamic and ever-evolving application landscape sound like a dream to us, right? It’s now a reality!
A sales colleague might integrate a marketing app that inadvertently synchronises confidential leads with an external database. These scenarios do not arise from malicious intent. Instead, they are the natural consequence of a busy, decentralised environment and the easy availability of cloud-based tools.
It’s more common than you think. Nudge will show you applications your team uses that have suffered data breaches.
One of your suppliers has been hacked, and your customer’s data is leaked. You’re now on the front page of the news. Your customers are suing you. Your Insurance might not cover you. Your directors are personally and financially liable. These terrifying statements could be avoided by managing your cloud applications with Nudge.
You can avoid that for the price of a cup of coffee per user per month.
Can you confidently tell if any of these typical applications have leaked your data?

We spoke earlier about a scenario where your staff uses three different project management tools for the same purpose – to serve your customers. Are you paying for all of them? What happens if you pick one service and cancel the others? Can you save money?
You can find all of this out by signing up for free and then we can take you through operatioanlising using the tool (or we manage it on your behalf) to keep your application usage lean, relevant, cost effective and secure.

In this article, we highlighted that a lack of control also makes it difficult to maintain alignment with security standards and practices.
The Essential 8 provides a guideline for safeguarding information, but it is nearly impossible to enforce measures without knowing which applications your staff uses.
If you cannot track who has access to which systems, you cannot ensure robust authentication methods, data retention policies, or vendor risk assessments.
Automatically discovering every connected application provides a clear, data-driven picture of your SaaS ecosystem. With that information, you can prioritise which services to investigate, enforce appropriate authentication controls, and ensure that your most sensitive data remains within approved and secure applications. Over time, this enhanced visibility makes consolidating technologies easier, reducing wasted spend on underutilised licences and strengthening your overall posture. You can even save money with Nudge Security! Modern organisations thrive on flexibility and efficiency, but unmanaged SaaS usage erodes both.
By partnering with Nudge Security, we help our customers achieve control over their application landscape. Better governance means lower risk, improved compliance, and a more agile environment. Rather than chasing problems after the fact, you can make informed decisions before issues occur.
Nudge Security offers a way to discover, secure, and govern your entire SaaS estate. We believe in their technology, approach, and commitment to simplifying a complex challenge. This is why we have chosen to recommend Nudge Security to our customers. Together, we can reduce shadow IT, improve data security, and ensure that your applications serve your business rather than complicate it.
We encourage you to explore Nudge Security and consider the advantages of greater SaaS visibility. It is time to end the guesswork, reduce complexity, and take control of your environment. Let’s embrace Nudge Security and create a more secure, efficient future for your organisation.

Chief Customer Officer
Mark Boyd is a Chief Customer Officer (CCO), plays a key executive role responsible for overseeing the entire customer experience within alltasksIT. The CCO serves as the voice of the customer at the highest levels of the company, ensuring that customer-centric strategies are developed and implemented across all departments.