
AvePoint Storage Optimisation
AvePoint Storage Optimisation Mark Boyd Chief Customer Officer A word from the author I have

AvePoint Storage Optimisation Mark Boyd Chief Customer Officer A word from the author I have

SIEM What Now? Mark Boyd Chief Customer Officer A word from the author I’ve spent

SolarWinds Service Desk Mark Boyd Chief Customer Officer A word from the author After two

Empower Your Business with Microsoft 365 E5 Microsoft 365 E5 is the premium tier of

Password Managers, In our digital age, where every click, swipe, and login leaves a digital

Empowering Sales Professionals with Power BISales professionals know the importance of strategically planning client and
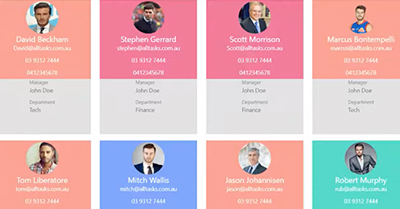
Need a quick way to find colleagues? This solution pulls user accounts from your active
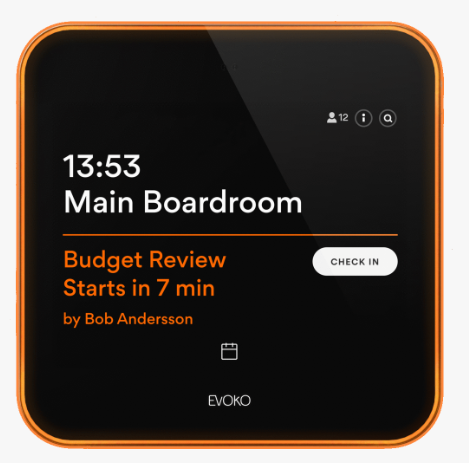
With Evoko Liso you can finally eliminate meeting room confusion, double bookings, and unnecessary interruptions to your meetings. Gone are the days of people tapping on your

DON’T LIKE REPEATING YOURSELF? Well actually, neither do we! Here at alltasksIT we’re always on
Everyone likes to be appreciated and feel valued in the workplace. Yammer helps connect